Release 2 (9.2)
Part Number A96573-01
Home |
Book List |
Contents |
Index |
 Master Index |
 Feedback |
| Oracle Advanced Security Administrator's Guide Release 2 (9.2) Part Number A96573-01 |
|
This chapter describes how to configure Oracle Advanced Security for the Oracle9i server, for use with RADIUS (Remote Authentication Dial-In User Service). This chapter contains the following topics:
RADIUS is a client/server security protocol widely used to enable remote authentication and access. Oracle Advanced Security uses this industry standard in a client/server network environment.
You can enable the network to use any authentication method that supports the RADIUS standard, including token cards and smart cards, by installing and configuring the RADIUS protocol. Moreover, when you use RADIUS, you can change the authentication method without modifying either the Oracle client or the Oracle database server.
From the user's perspective, the entire authentication process is transparent. When the user seeks access to an Oracle database server, the Oracle database server, acting as the RADIUS client, notifies the RADIUS server. The RADIUS server:
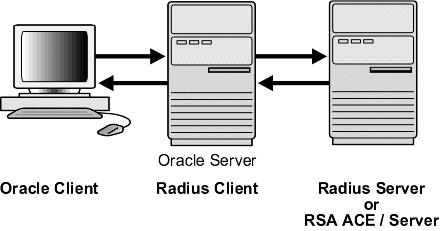
The Oracle/RADIUS environment is displayed in Figure 4-1:
Text description of the illustration asoag003.gif
The Oracle database server acts as the RADIUS client, passing information between the Oracle client and the RADIUS server. Similarly, the RADIUS server passes information between the Oracle database server and the appropriate authentication servers. The authentication components are listed in Table 4-1:
A RADIUS server vendor is often the authentication server vendor as well, in which case authentication can be processed on the RADIUS server. For example, the RSA ACE/Server is both a RADIUS server and an authentication server. It thus authenticates the user's passcode.
| See Also:
Oracle9i Net Services Administrator's Guide, for information about the |
User authentication can take place in either of two ways:
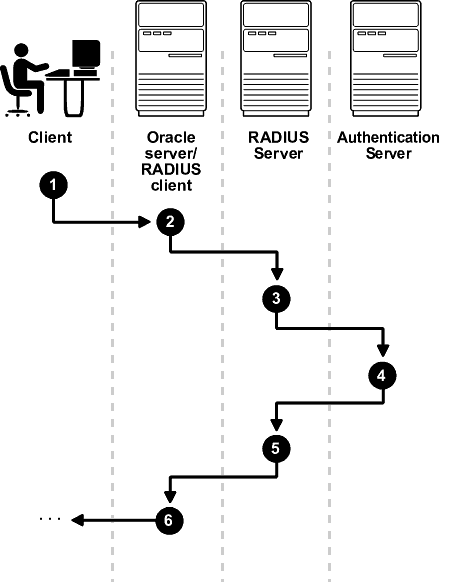
In the synchronous mode, RADIUS lets you use various authentication methods, including passwords and SecurID token cards. Figure 4-2 shows the sequence in which synchronous authentication occurs:
Text description of the illustration ano81010.gif
With SecurID authentication, each user has a token card that displays a dynamic number that changes every sixty seconds. To gain access to the Oracle database server/RADIUS client, the user enters a valid passcode that includes both a personal identification number (PIN) and the dynamic number currently displayed on the user's SecurID card. The Oracle database server passes this authentication information from the Oracle client to the RADIUS server, which in this case is the authentication server for validation. Once the authentication server (RSA ACE/Server) validates the user, it sends an "accept" packet to the Oracle database server, which, in turn, passes it to the Oracle client. The user is now authenticated and able to access the appropriate tables and applications.
See Also:
|
When the system uses the asynchronous mode, the user does not need to enter a user name and password at the SQL*Plus CONNECT string. Instead, a graphical user interface asks the user for this information later in the process.
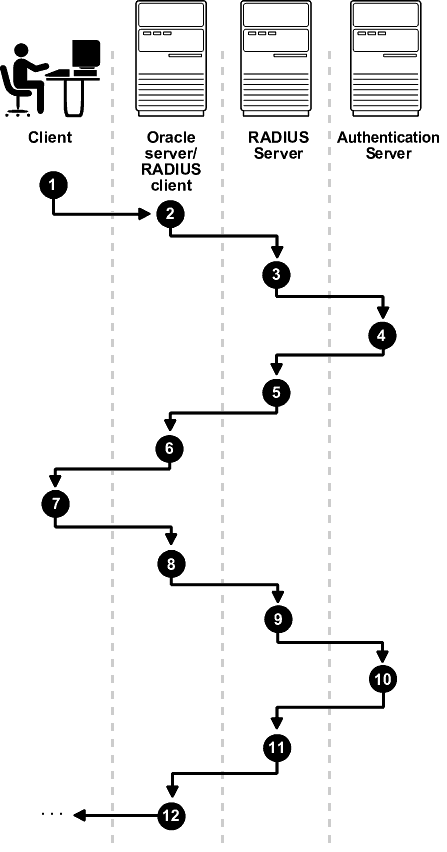
Figure 4-3 shows the sequence in which challenge-response (asynchronous) authentication occurs.
|
Note: If the RADIUS server is the authentication server, Steps 3, 4, and 5, and Steps 9, 10, and 11 in Figure 4-3 are combined. |
Text description of the illustration ano81011.gif
With smart card authentication, the user logs in by inserting the smart card--a plastic card (like a credit card) with an embedded integrated circuit for storing information--into a hardware device which reads the card. The Oracle client sends the login information contained in the smart card to the authentication server by way of the Oracle database server/RADIUS client and the RADIUS server. The authentication server sends back a challenge to the Oracle client, by way of the RADIUS server and the Oracle database server, prompting the user for authentication information. The information could be, for example, a PIN as well as additional authentication information contained on the smart card.
The Oracle client sends the user's response to the authentication server by way of the Oracle database server and the RADIUS server. If the user has entered a valid number, the authentication server sends an "accept" packet back to the Oracle client by way of the RADIUS server and the Oracle database server. The user is now authenticated and authorized to access the appropriate tables and applications. If the user has entered incorrect information, the authentication server sends back a message rejecting the user's access.
One particular ActivCard token is a hand-held device with a keypad and which displays a dynamic password. When the user seeks access to an Oracle database server by entering a password, the information is passed to the appropriate authentication server by way of the Oracle database server/RADIUS client and the RADIUS server. The authentication server sends back a challenge to the client--by way of the RADIUS server and the Oracle database server. The user types that challenge into the token, and the token displays a number for the user to send in response.
The Oracle client then sends the user's response to the authentication server by way of the Oracle database server and the RADIUS server. If the user has typed a valid number, the authentication server sends an "accept" packet back to the Oracle client by way of the RADIUS server and the Oracle database server. The user is now authenticated and authorized to access the appropriate tables and applications. If the user has entered an incorrect response, the authentication server sends back a message rejecting the user's access.
To enable RADIUS authentication and accounting, perform the following tasks:
RADIUS is installed with Oracle Advanced Security during a typical installation of Oracle9i.
| See:
Oracle9i operating system-specific installation documentation, for information about installing Oracle Advanced Security and the RADIUS adapter |
This task includes the following steps:
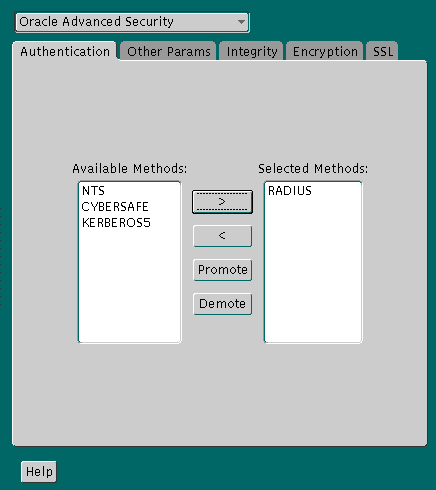
Unless otherwise indicated, perform these configuration tasks by using Oracle Net Manager or by using any text editor to modify the sqlnet.ora file.
Text description of the illustration radu0001.gif
The sqlnet.ora file is updated with the following entry:
SQLNET.AUTHENTICATION_SERVICES=(RADIUS)
$ORACLE_HOME/network/security on UNIX or ORACLE_HOME\network\security on Windows NT.radius.key to hold the shared secret copied from the RADIUS server. Place the file in the directory you just created in Step 2.radius.key to read only, accessible only by the Oracle owner (Oracle relies on the file system to keep this file secret).
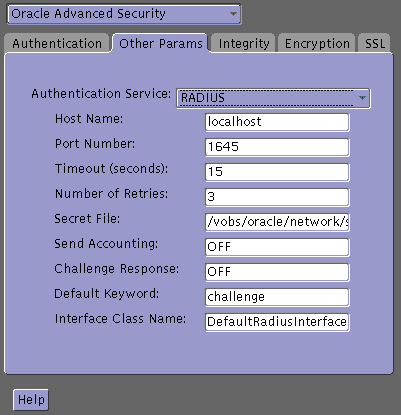
localhost as the default primary RADIUS server, or enter another host name.The sqlnet.ora file is updated with the following entries:
SQLNET.AUTHENTICATION_SERVICES=RADIUS
SQLNET.RADIUS_AUTHENTICATION=RADIUS_server_{hostname|IP_address}
Configure the initialization parameter file, located in
with the following values:
REMOTE_OS_AUTHENT=FALSEOS_AUTHENT_PREFIX=""
| See Also:
Oracle9i Database Reference and the Oracle9i Database Administrator's Guide, for information about setting initialization parameters on the Oracle9i database server |
| Field | Description |
|---|---|
|
Port Number |
Specifies the listening port of the primary RADIUS server. The default value is 1645. |
|
Timeout (seconds) |
Specifies the time the Oracle database server waits for a response from the primary RADIUS server. The default is 15 seconds. |
|
Number of Retries |
Specifies the number of times the Oracle database server resends messages to the primary RADIUS server. The default is three retries. For instructions on configuring RADIUS accounting, see: Task 5: Configure RADIUS Accounting. |
|
Secret File |
Specifies the location of the secret key on the Oracle database server. The field specifies the location of the secret key file, not the secret key itself. For information about specifying the secret key, see: Create the RADIUS Secret Key File on the Oracle Database Server. |
The sqlnet.ora file is updated with the following entries:
SQLNET.RADIUS_AUTHENTICATION_PORT=(PORT)SQLNET.RADIUS_AUTHENTICATION_TIMEOUT=
(NUMBER OF SECONDS TO WAIT FOR response)SQLNET.RADIUS_AUTHENTICATION_RETRIES=
(NUMBER OF TIMES TO RE-SEND TO RADIUS server)SQLNET.RADIUS_SECRET=(path/radius.key)
The challenge-response (asynchronous) mode presents the user with a graphical interface requesting first a password, then additional information--for example, a dynamic password that the user obtains from a token card. With the RADIUS adapter, this interface is Java-based to provide optimal platform independence.
| See Also:
Appendix C, Integrating Authentication Devices Using RADIUS, for information about how to customize the challenge-response user interface |
To configure challenge-response:
DefaultRadiusInterface or enter the name of the class you have created to handle the challenge-response conversation. If other than the default RADIUS interface is used, you also must edit the sqlnet.ora file to enter SQLNET.RADIUS_CLASSPATH=(location), where location is the complete path name of the jar file. It defaults to$ORACLE_HOME/network/jlib/netradius.jar: $oracle_home/JRE/lib/vt.jarThe sqlnet.ora file is updated with the following entries:
SQLNET.RADIUS_CHALLENGE_RESPONSE=([ON | OFF])SQLNET.RADIUS_CHALLENGE_KEYWORD=(KEYWORD)SQLNET.RADIUS_AUTHENTICATION_INTERFACE=(name of interface including the package name delimited by "/" for ".")
If you are using an alternate RADIUS server, set these parameters in the sqlnet.ora file using any text editor.
SQLNET.RADIUS_ALTERNATE=(hostname or ip address of alternate radius server)SQLNET.RADIUS_ALTERNATE_PORT=(1812)SQLNET.RADIUS_ALTERNATE_TIMEOUT=(number of seconds to wait for response)SQLNET.RADIUS_ALTERNATE_RETRIES=(number of times to re-send to radius server)
To grant user access:
SQL> CONNECT system/manager@database_name;SQL> CREATE USER username IDENTIFIED EXTERNALLY;SQL> GRANT CREATE SESSION TO USER username;SQL> EXIT
If you are using Windows NT, you can use the Security Manager tool in the Oracle Enterprise Manager.
If you require external RADIUS authorization for RADIUS users who connect to an Oracle database, then you must perform the following steps to configure the Oracle server, the Oracle client, and the RADIUS server:
OS_ROLE parameter to the init.ora file and set this parameter to TRUE as follows:
OS_ROLE=TRUE
Then restart the database so the system can read the change to the init.ora file.
ON for the server if you have not already done so by following the steps listed in "Configure Challenge-Response".Set the RADIUS challenge-response mode to ON for the client if you have not already done so by following the steps listed in "Configure Challenge-Response".
| ATTRIBUTE NAME | CODE | TYPE |
|---|---|---|
|
|
26 |
Integer |
|
|
1 |
String |
For example, enter the following in the RADIUS server attribute configuration file:
VALUE VENDOR_SPECIFIC ORACLE 111
ORACLE_ROLE attribute to the user profile of the users who will use external RADIUS authorization:
ORA_databaseSID_rolename[_[A]|[D]]
where:
ORA designates that this role is used for Oracle purposesdatabaseSID is the Oracle system identifier that is configured in the database server's init.ora filerolename is the name of role as it is defined in the data dictionary. For example, SYSDBAA is an optional character that indicates the user has adminstrator's privileges for this roleD is an optional character that indicates this role is to be enabled by defaultEnsure that RADIUS groups which map to Oracle roles adhere to the ORACLE_ROLE syntax.
For example:
USERNAMEUSERPASSWD="user_password", SERVICE_TYPE=login_user, VENDOR_SPECIFIC=ORACLE, ORACLE_ROLE=ORA_ora920_sysdba
RADIUS accounting logs information about access to the Oracle database server and stores it in a file on the RADIUS accounting server. Use this feature only if both the RADIUS server and authentication server support it.
To enable or disable RADIUS accounting:
The sqlnet.ora file is updated with the following entry:
SQLNET.RADIUS_SEND_ACCOUNTING= ON
RADIUS Accounting consists of an accounting server residing on either the same host as the RADIUS authentication server or on a separate host.
| See Also:
Administration documentation for the RADIUS server, for information about configuring RADIUS accounting |
You can use virtually any RADIUS server that complies with the standards in the Internet Engineering Task Force (IETF) RFC #2138, Remote Authentication Dial In User Service (RADIUS) and RFC #2139 RADIUS Accounting. Because RADIUS servers vary, consult the documentation for your particular RADIUS server for any unique interoperability requirements.
Perform the following steps to add the RADIUS client name to a Livingston RADIUS server:
@ (#) clients 1.1 2/21/96 Copyright 1991 Livingston Enterprises IncThis file contains a list of clients which are allowed to make authentication requests and their encryption key. The first field is a valid hostname. The second field (separated by blanks or tabs) is the encryption key.Client Name Key
CLIENT NAME column, enter the host name or IP address of the host on which the Oracle database server is running. In the KEY column, type the shared secret.
The value you enter in the CLIENT NAME column, whether it is the client's name or IP address, depends on the RADIUS server.
See the authentication server documentation for instructions about configuring the authentication servers.
| See Also:
"Related Documentation", which contains a list of possible resources. |
See the RADIUS server documentation.
If the RADIUS server supports vendor type attributes, you can manage roles by storing them in the RADIUS server. The Oracle database server downloads the roles when there is a CONNECT request using RADIUS.
To use this feature, configure roles on both the Oracle database server and the RADIUS server.
Perform these steps to configure roles on the Oracle database server:
OS_ROLES parameter in the initialization parameters file on the Oracle database server.To configure roles on the RADIUS server, refer to Table 4-1 and use the following syntax:
ORA_DatabaseName.DatabaseDomainName_RoleName
Example:
ORA_USERDB.US.ORACLE.COM_MANAGER
To configure challenge-response mode, See:
If you are using the synchronous authentication mode, launch SQL*Plus and enter the following command at the prompt:
CONNECT username/password@database_alias
Note that you can log in with this command only when challenge-response is not turned to ON.
If you are using the challenge-response mode, launch SQL*Plus and, at the prompt, enter the command that follows:
CONNECT /@database_alias
Note that you can log in with this command only when challenge-response is turned to ON.
If you are using an RSA ACE/Server as a RADIUS server, check the following items before making your initial connection:
|
 Copyright © 1996, 2002 Oracle Corporation. All Rights Reserved. |
|