Release 2 (9.2)
Part Number A96578-01
Home |
Book List |
Contents |
Index |
 Master Index |
 Feedback |
| Oracle Label Security Administrator's Guide Release 2 (9.2) Part Number A96578-01 |
|
Oracle Label Security enables application developers to add label-based access control to their Oracle9i applications. It mediates access to rows in database tables based on a label contained in the row, and the label and privileges associated with each user session. Oracle Label Security is built on the virtual private database technology of Oracle9i Enterprise Edition. It includes the Oracle Policy Manager, a graphical user interface for ease of administration.
This chapter introduces Oracle Label Security in the larger context of data security. It contains the following sections:
| See Also:
For a complete introduction to Oracle9i features and terminology, see Oracle9i Database Concepts |
This section introduces basic concepts of computer security. It contains the following topics:
Computer security involves the protection of computerized data and processes from unauthorized modification, destruction, disclosure, or delay. In the Internet age, the risks to valuable and sensitive data are greater than ever before. Figure 1-1 shows the complex computing environment that your data security plan must encompass.
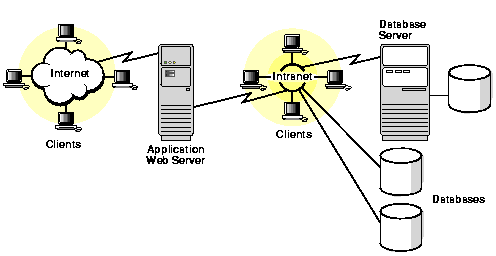
You must protect databases and the servers on which they reside; you must administer and protect the rights of internal database users; and you must guarantee the confidentiality of electronic commerce customers as they access your database. Oracle Corporation provides products to address the full spectrum of computer security issues.
Oracle Corporation strives to create products which meet stringent international security standards. Security evaluation is a formal assessment process performed by independent bodies against national and international criteria. It provides external and objective assurance that a system meets the security criteria for which it was designed. Upon successful completion of an evaluation, a security rating is assigned to the system or product. This certification provides confidence in the security of information technology products and systems to commercial, government and military users.
Oracle9i is designed to meet the Database Management System Protection Profile (DBMS PP). Oracle Label Security is designed for evaluation under the ISO/IEC 15408 Common Criteria.
A database security policy is an implementation of an overall system security policy, which in turn is often derived from a broad, organizational security policy. The overall security policy can include:
Access control is the process of defining a user's ability to read or write information. Application developers must decide which approach to access control best meets their needs.
Oracle9i provides discretionary access control (DAC). DAC is a means of controlling access to information through privileges, which are permissions to perform an operation within the system. On a table-by-table basis, DAC provides the SELECT, INSERT, UPDATE, and DELETE privileges. These privileges authorize the corresponding SQL operation upon the table.
With discretionary access control, access to data is controlled in a single dimension. The administrator grants users privileges which determine the operations (such as read, write) they can perform upon data. A subject, defined as a user and the processes or tasks running on behalf of that user, must have the appropriate privilege, such as the SELECT privilege, to access an object, such as a table or view. A user must first have the necessary DAC privileges to access data in an object.
In Oracle9i, row-level access control is available with the virtual private database (VPD) technology which is a standard feature of the Enterprise Edition. Virtual private database provides fine-grained access control which is data-driven, context-dependent, and row-based. You can implement VPD by writing a stored procedure to append a SQL predicate to each SQL statement to control row level access for that statement. For example, if John Doe (who belongs to Department 10) inputs the statement SELECT * FROM emp, you can use VPD to tack on the clause WHERE DEPT = 10. In this way query modification is used to restrict data access to certain rows.
Label-based access is a way of controlling data on a row level. Each data row is given a label used to store information about data sensitivity. A label provides additional sophisticated access control rules in addition to those provided by discretionary access control. It further mediates access to a data row based on the identity and label of the user and the label of the row. This provides an additional level of access control to a system.
Label-based access control depends on the basic DAC policy; together these policies dictate the criteria by which access to an object is either permitted or denied. In most applications, a relatively small number of application tables will require label-based access controls. The protection provided by standard DAC will suffice for a majority of application tables.
To be allowed access to a row, a user must satisfy both Oracle Label Security and Oracle9i DAC requirements. Oracle9i enforces DAC based on the user's system-level privileges and database object privileges. First a user must be authenticated to the Oracle9i database. Second, the user must have the DAC object and system privileges required for the operation.
Finally, the user must meet the criteria added by Oracle Label Security. This product adheres to the label definitions, label hierarchies, and other security policy rules defined within the database by the site administrators. On top of this, Oracle Label Security enforces access based on the labels of the user and row, as well as the user's Oracle Label Security policy privileges.
Oracle Label Security is flexible and functional enough to support applications in a variety of production environments. It supports Oracle9i data integrity, availability, and recovery capabilities, as well as user accountability and auditing, while enforcing a site's security policy.
Oracle Label Security is built on the virtual private database (VPD) technology found in the Oracle9i Enterprise Edition. It also uses the Application Context functionality of this product.
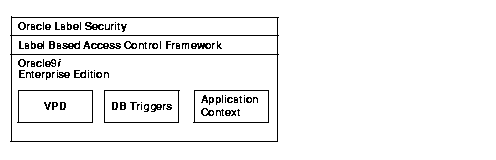
VPD supports fine-grained access control to data rows. It provides an application programmatic interface (API) which allows security policies to be assigned to database tables and views. Using PL/SQL, developers and security administrators can create security policies with stored procedures, and bind the procedures to a table or view by means of a call to an RDBMS package. Such policies are based on the content of application data stored within the Oracle9i database, or based on context variables provided by Oracle9i. In this way, VPD permits access security mechanisms to be removed from applications, and centralized within Oracle9i.
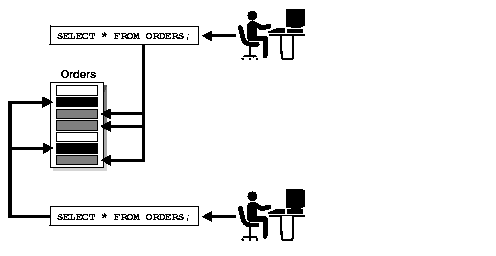
As illustrated in Figure 1-3, VPD lets you associate security conditions with tables or views. In this example, when each user selects from the ORDERS table, the appropriate security condition is automatically enforced. The server automatically enforces security policies, no matter how the data is accessed. In this way, VPD eliminates the need to use many views to implement security.
Oracle Label Security provides a functional, out-of-the-box VPD policy which enhances your ability to implement row-level security. It supplies an infrastructure--a label-based access control framework--whereby you can specify labels for users and data. It also enables you to create one or more custom security policies to be used for label access decisions. You can implement these policies without any knowledge of a programming language. There is no need to write additional code; in a single step you can apply a security policy to a given table. In this way, Oracle Label Security provides a straightforward, efficient way to implement fine-grained security policies using data labeling technology. Finally, the structure of Oracle Label Security labels provides a degree of granularity and flexibility which cannot easily be derived from the application data alone. Oracle Label Security is thus a generic solution which can be used in many different circumstances.
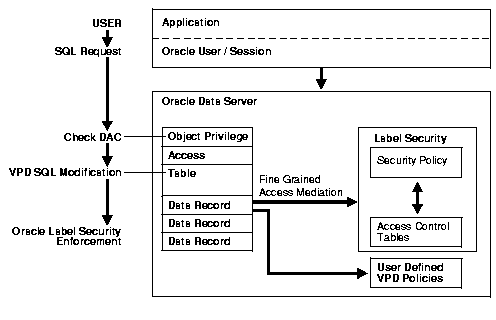
Figure 1-4 illustrates the process by which data is accessed under Oracle Label Security. Within an application and Oracle9i session, a user issues a SQL request. Oracle9i checks the DAC privileges, making sure the user has SELECT privileges on the table. Then it checks to see if a VPD policy has been attached to the table. It finds that the table is protected by Oracle Label Security. The SQL statement is modified on the fly.
Each data record has a label; Oracle Label Security is invoked for each row, to determine whether, based on the label, the user can or cannot access the row.
Oracle Label Security provides additional row level security access controls to the underlying Oracle9i database. This section contains these topics:
To create a customized Oracle Label Security policy, you define a set of labels and a set of rules that govern data access, based on these labels.
For example, assume that a user has SELECT privilege on an application table. As illustrated in Figure 1-5, when the user executes a SELECT statement, Oracle Label Security evaluates each row selected and determines whether the user can access it based on the privileges and access labels assigned to the user by the security administrator. Oracle Label Security can also be configured to perform security checks on UPDATE, DELETE, and INSERT statements.
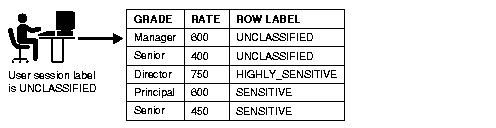
Oracle Label Security adds label-based access controls to the Oracle9i object-relational database management system. Access to data is mediated based on these factors:
Consider, for example, a standard Data Manipulation Language operation (such as SELECT) performed upon a row of data. When evaluating this access request by a user with the CONFIDENTIAL label, to a data row labeled CONFIDENTIAL, Oracle Label Security determines that this access can, in fact, be achieved.
In this way, data of different sensitivities--or belonging to different companies--can be stored and managed on a single system, while preserving data security through standard Oracle access controls. Likewise, applications from a broad range of industries can use row labels to provide additional access control functionality where necessary.
In Oracle Label Security, each row of a table can be labeled as to its level of confidentiality. The label contains three components:
The level specifies the sensitivity of the data. A typical government organization might define levels CONFIDENTIAL, SENSITIVE, and HIGHLY_SENSITIVE. A commercial organization might define a single level for COMPANY_CONFIDENTIAL data. The compartment component is non-hierarchical; compartments are typically defined to segregate data--such as data related to an ongoing strategic initiative. Finally, groups are used to record ownership and can be used hierarchically. For example, FINANCE and ENGINEERING groups can be defined as children of the CEO group, creating an ownership relation.
Labels can contain a single level component, a level combined with a set of either compartments or groups, or a level with both compartments and groups.
Users can be granted label authorizations which determine what kind of access (read or write) they have to the rows that are labeled.
Policy privileges enable a user or stored program unit to bypass aspects of the label-based access control policy. In addition, the administrator can authorize the user or program unit to perform specific actions, such as the ability of one user to assume the authorizations of a different user.
Privileges can be granted to program units, authorizing the procedure, rather than the user, to perform privileged operations. When only stored program units--and not individual users--have Oracle Label Security privileges, your system is most secure. Further, such program units encapsulate the policy, which minimizes the amount of application code that needs to be reviewed for security.
In Oracle Label Security you can apply different enforcement options for maximum flexibility in controlling the different Data Manipulation Language operations that users can perform. For each operation--SELECT, INSERT, UPDATE, and DELETE--you can specify a particular type of enforcement of the security policy, for each table. In this way you can customize the label-based access controls on each table.
When label-based access is enforced, a user's label must meet certain criteria, determined by policy definitions, to access a row within a protected table. These access controls act as a secondary access mediation check, on top of the discretionary access controls which have been implemented by the application developers.
In summary, Oracle Label Security provides four aspects of label-based access control:
Oracle Label Security supplements the Oracle9i audit facility by tracking the use of its own Oracle Label Security administrative operations and policy privileges. Under Oracle Label Security, audit trail records contain a label associated with the session that generated the audit, so that you can see the relationship between operations, data labels, and the label of the user performing the operation.
Oracle Label Security supports distributed operation when labels in the local and remote databases are compatible.
|
 Copyright © 2000, 2002 Oracle Corporation. All Rights Reserved. |
|