Release 2 (9.2)
Part Number A96573-01
Home |
Book List |
Contents |
Index |
 Master Index |
 Feedback |
| Oracle Advanced Security Administrator's Guide Release 2 (9.2) Part Number A96573-01 |
|
This chapter describes how to use Oracle Enterprise Security Manager to administer Enterprise User Security in Oracle9i databases. This chapter contains the following topics:
Oracle Enterprise Security Manager, a component of Oracle Enterprise Manager, is an administration tool employed by Oracle Advanced Security to manage enterprise users, enterprise domains, databases, and enterprise roles that are held in an LDAP-compliant directory service.
The directory service is used as a central repository to define user and server access information for a network. It stores naming information, global password definitions, PKI credentials, and application access authorizations for the users that it defines. Such centralized storage of enterprise users and their access privileges supports single sign-on capability, and provides secure, scalable user administration.
The following tasks describe how to use Oracle Enterprise Security Manager to install Oracle Management Server and Oracle Enterprise Manager:
Oracle9i Enterprise User Security is based on an LDAP-compliant directory. The directory server must be properly installed and configured before Oracle Enterprise Manager can be used to manage Enterprise User Security. The following elements of directory configuration must be completed before proceeding:
Oracle Enterprise Manager is automatically installed by the Oracle9i Enterprise Edition server installation process, and includes all necessary functionality to support Enterprise User Security. Oracle Enterprise Manager is also installed by default with the Oracle9i infrastructure installation at the same time as Oracle Internet Directory. Oracle Enterprise Manager can also be installed separately in its own ORACLE_HOME, using the custom install option.
To launch Oracle Enterprise Security Manager, use one of the following options:
From the Enterprise Manager ORACLE_HOME, enter the following at the command line:
esm
Choose Start > Programs > Oracle - HOME_NAME > Integrated Management Tools > Enterprise Security Manager
The directory login box appears (Figure 19-1):
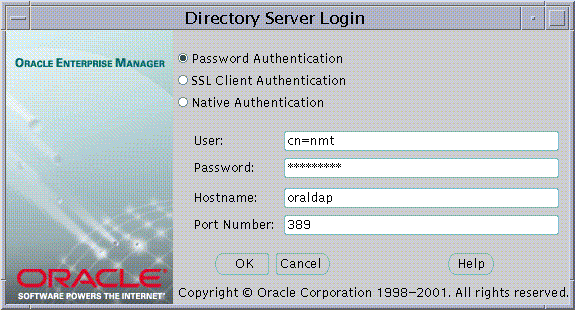
Text description of the illustration esm0001.gif
Oracle Enterprise Security Manager provides three ways to connect to a directory server, summarized by Table 19-1:
| Authentication Method | Description |
|---|---|
|
Password Authentication |
Uses simple authentication requiring a distinguished name (DN) or a known directory UserID and a password (that is, the user name and password). |
|
SSL Client Authentication |
Uses two-way SSL authentication in which both the client and server use Oracle Wallets containing digital certificates (that is, the user name and certificate). The subsequent connection is encrypted. |
|
Native Authentication |
Applies to Microsoft Windows NT and Windows 2000 only; uses operating system-level authentication to log on to a Microsoft Active Directory. |
To select an authentication method, choose the appropriate option in the Directory Server Login Window (Figure 19-1).
Oracle Enterprise Security Manager manages one directory server, identified at the top of the main application tree. It lets you manage users and Oracle Contexts in the directory. An Oracle Context is a subtree in a directory recognizable to Oracle products. It provides an administrative hierarchy for management of Oracle data including installed Oracle products that access the directory.
This section describes how to use Oracle Enterprise Security Manager to administer enterprise users. It contains the following topics:
Use Oracle Enterprise Security Manager to create users in the directory.
To create new users, select Create Enterprise User... from the Operations menu. The Create User window appears (Figure 19-2).
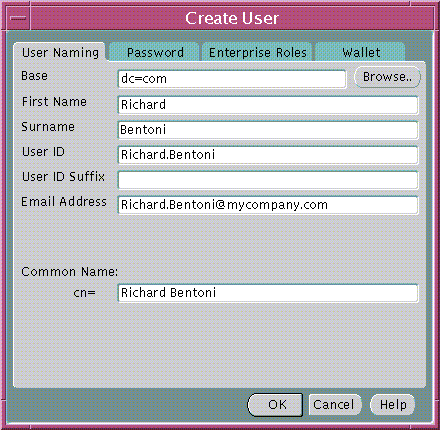
Text description of the illustration esm0005.gif
Referring to Table 19-2, enter the appropriate user information required by the User Naming tabbed window; choose OK to create a new enterprise user.
An enterprise user entry can reside at any base within the directory. The base can be any existing directory entry, such as country entry (c=us), or an organization entry (o=acme,c=us). Multiple users typically share the same directory base. This base associates all the users contained under it with the same high level organization in the hierarchy.
You can enter the base in the base field of the Create User window (Figure 19-2). Alternatively, you can browse the entire directory to select a suitable base by choosing the Browse... button (in the same window); the Browse Directory Window appears (Figure 19-3):
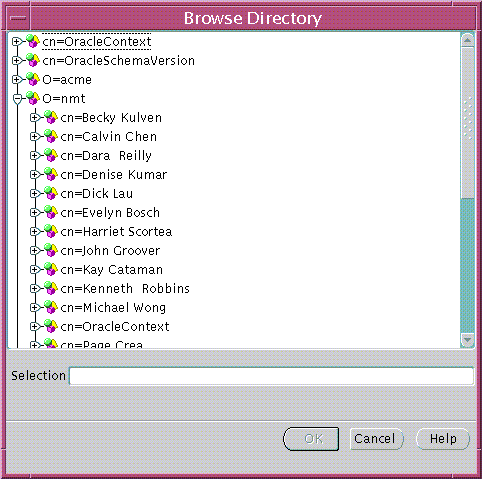
Text description of the illustration esm0006.gif
The Browse Directory window lets you navigate the directory by drilling down into each entry from the top of the directory tree. When a directory entry is selected its distinguished name (DN) is placed in the Selection field. To accept the selected Distinguished Name choose the OK button. This value is returned as the selected base for a new directory user, and is preserved for all subsequent operations that create or search for users in the directory--although you can change it from time to time.
The Password tab of the Create User Window (Figure 19-4) lets you define and maintain the enterprise user password:
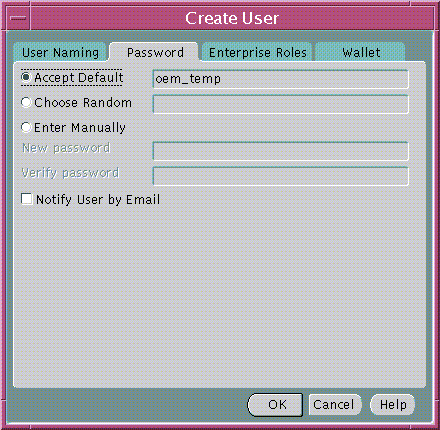
Text description of the illustration esm0007.gif
The enterprise user password is used for:
When creating a new password, you can choose one of the following options:
To send the password to the new user by e-mail, select Notify User by Email, and instruct the new user to change the password after its first use. The e-mail address from the User Naming tab in Figure 19-2 is used.
When you create a new enterprise user, you can grant any previously configured enterprise roles to a new user.
To select one or more enterprise roles to grant to a new user, choose the Add... button on the Enterprise Roles tab of the Create User window.
The Add Enterprise Roles window appears (Figure 19-5):
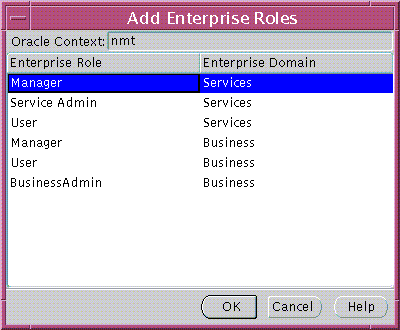
Text description of the illustration esm0009.gif
Select the correct Oracle Context, then select any enterprise roles in your Oracle Context to assign to the new user; choose OK.
A sample Oracle Wallet containing a new digital certificate, private key, and certificate trust points may be generated for the new user in an encrypted binary format. The Oracle Wallet will be stored with the new user in the directory server as part of the directory entry for the user. To create a sample wallet for new users, choose the Wallet tab of the Create User window (Figure 19-6).
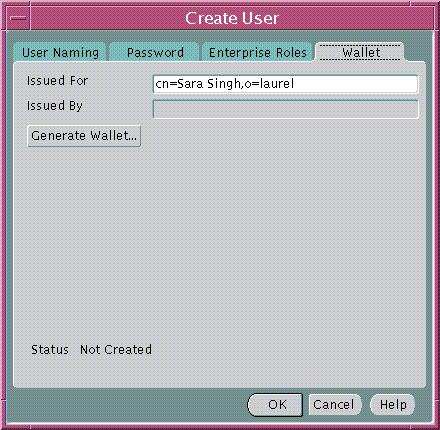
Text description of the illustration esm0037.gif
The distinguished name (DN) under which the new User will be created is used by default as the DN for the digital certificate to be contained in the new user's Oracle wallet. The user cannot connect to the database if the DNs of user certificates are not equal to their DNs in the directory. However, you may edit the DN to be used for the certificate before generating the wallet by editing the contents of the Issued For: field.
A sample Oracle wallet will be created when you click the Generate Wallet... button. When you select a user from the Edit User window (see Figure 19-8) a userpkcs12 attribute is visible in the attribute list of that user. The userpkcs12 attribute represents the wallet created in this step.
Oracle Enterprise Security Manager lets you browse the directory for all users currently stored.
To browse enterprise users, choose the All Users tab in the main window (Figure 19-7):
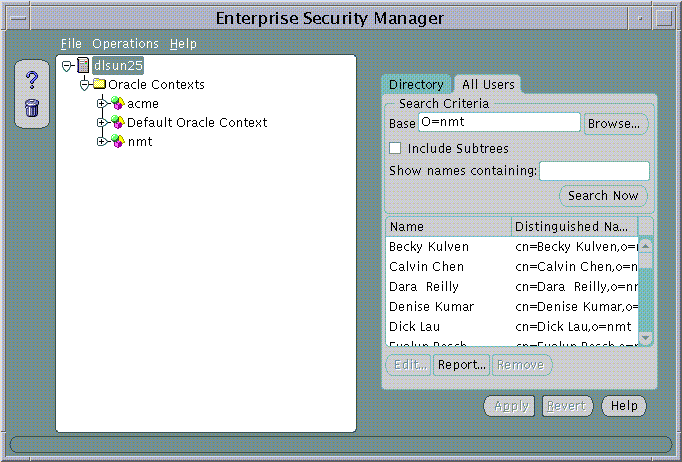
Text description of the illustration esm0011.gif
To search for users in the directory, define the search criteria and choose the Search Now button. The window displays the results of the search. Table 19-3 summarizes the search criteria and their respective effects on the search results:
Example:
Selecting a user from the search results for editing.
To edit one of the returned user names, select the target user name and choose the Edit... button--or just double-click the target user name in the list (Figure 19-8):
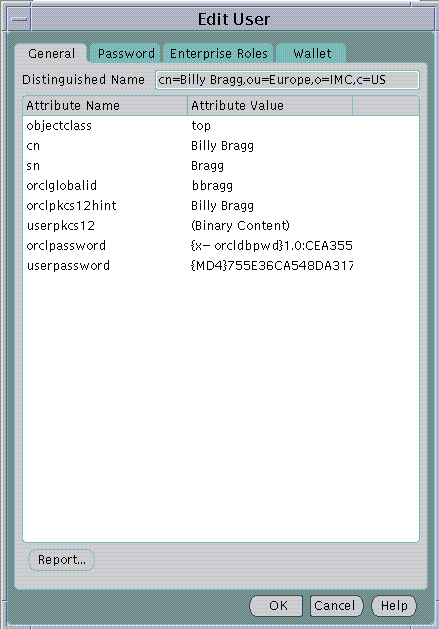
Text description of the illustration esm0013.gif
When you select a directory user for edit, you can change the password and enterprise role assignments--and you can modify the user wallet in the same manner as during its initial creation.
The user entry must reside in a directory subtree of users that has been enabled for Oracle database access. You can set Oracle Database Access permissions for a selected subtree--to let databases within a domain in the Password-Accessible Domains group read the user's login credentials.
To enable database access:
On a selected subtree of directory users, set Oracle Database Access permissions to permit databases in the Password-Accessible Domains group to access the user's database login credentials:
An Oracle Context is a subtree in a directory that contains the data used by any installed Oracle product that uses the directory. Oracle Enterprise Security Manager is one such product. It lets you manage database and security-related information in the directory, in an Oracle Context.
Oracle Enterprise Security Manager can support multiple Oracle Contexts in a directory, including Oracle8i and Oracle9i versions. However, Oracle9i Enterprise User Security can only be managed using an Oracle9i Oracle Context. Oracle Enterprise Security Manager for Oracle9i may be used to manage version 9i Oracle Contexts as well version 8i Oracle Contexts in the directory.
Oracle Enterprise Security Manager displays all existing Oracle Contexts in its main application tree--including both Oracle8i and Oracle9i versions. In the following example (Figure 19-9), Oracle Enterprise Security Manager is connected to an Oracle directory that has been configured to support the Oracle9i directory schema and an Oracle9i root Oracle Context.
An Oracle Context has a number of properties that can be viewed and managed in the Enterprise Security Manager window (Figure 19-9, Table 19-4):
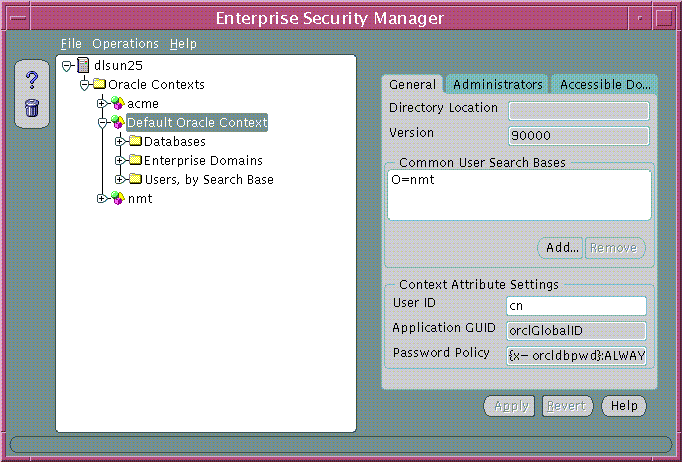
Text description of the illustration esm0014.gif
|
Note: The reference to Default Oracle Context in Figure 19-9 should read Root Oracle Context. |
To understand the properties of an Oracle Context, refer to Table 19-4:
Using Oracle Enterprise Security Manager to register a database with the directory is new in this release. You can also use Database Configuration Assistant to register a database with the directory. Table 19-5 lists the differences between using these two Oracle tools.
| See Also:
"About Registering the Database in the Directory" for more information about registering databases in the directory. |
If you want to generate a placeholder database wallet, then you must first run the following tool at the command line:
esm -genca
Follow the prompts that this tool displays. This tool creates a simulated certificate authority in your Oracle wallet directory.
If you need to edit the Connect String, then select Store TNS Connect String, which makes that field available for editing.
If you do not see the Generate Wallet option, then ensure that you have run the esm -genca tool that is described in "Prerequisites".
RDBMS_SERVER_DN parameter in the server parameter file (spfile.ora) by entering the following command at a SQL*Plus prompt:
ALTER SYSTEM SET RDBMS_SERVER_DN=SERVER_DN SCOPE SPFILE
Common user search bases can be added to or removed from an Oracle9i Oracle Context using the General tabbed window (Figure 19-9).
To remove a user search base from an Oracle Context:
To add a new user search base to an Oracle Context:
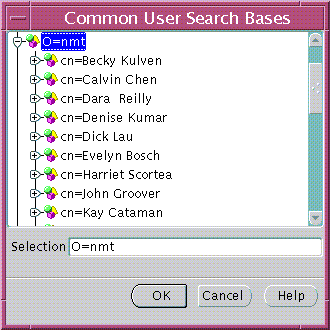
Text description of the illustration esm0015.gif
An Oracle Context contains administrative groups that have varying levels of privileges for operations within an Oracle Context. Some administrative groups are only available in Oracle9i Oracle Contexts and some are available in both Oracle8i and Oracle9i Oracle Contexts. The administrative groups for an Oracle Context are defined by Table 19-6:
Use the Administrators tab of the Oracle Enterprise Security Manager main window to manage Oracle Context Administrators(Table 19-11):
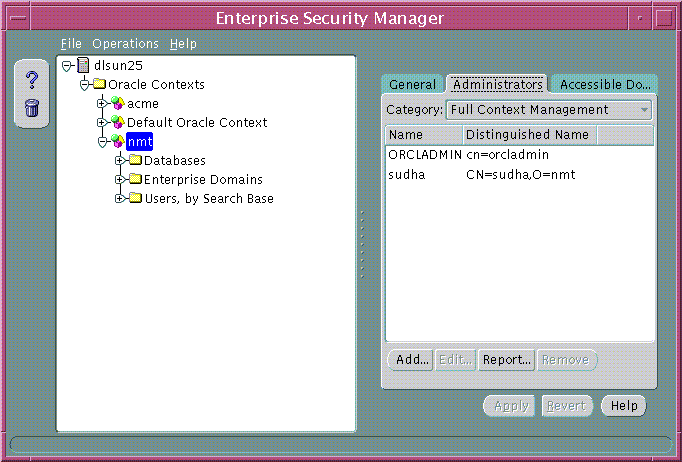
Text description of the illustration esm0016.gif
To remove a user from a list of Oracle Context Administrators:
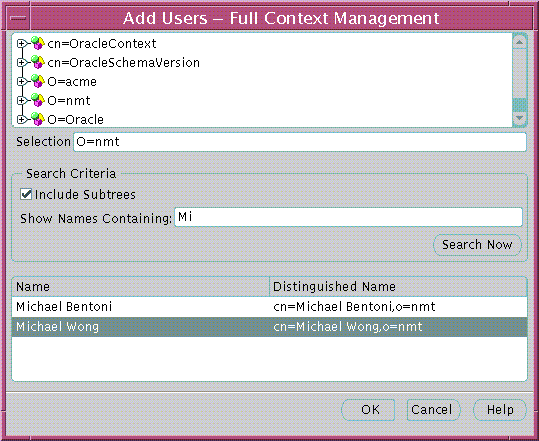
Text description of the illustration esm0017.gif
To add a new user to the list of Oracle Context Administrators:
Use this window to locate and select users in the directory. There are three panels in the window:
There are three requirements for a database to accept a connection from a password-authenticated user:
To configure password accessibility:
Once databases are registered in the directory, you can use Oracle Enterprise Security Manager to manage user access to those databases. This is achieved using the following objects in the Oracle Context (Table 19-7):
| Object | Description |
|---|---|
|
Database |
A directory entry representing a registered database. |
|
Enterprise Domain |
A grouping of databases registered in the directory, upon which a common user access model for database security can be implemented |
|
Enterprise Role |
An Authorization that spans multiple databases within an enterprise domain. It is an enterprise role to which individual roles can be granted on each of the databases in an enterprise domain. |
|
Mapping |
A mapping object is used to map the distinguished name (DN) of a user to a database schema that the user will access. |
A Database Administrator is a directory user that has privileges to modify the database and its subtree in the Oracle Context. Database Administrators may be managed using the Administrators tabbed window when a database is selected under an Oracle Context in the main application tree (Figure 19-11).
To remove a user from the list of Database Administrators:
To add a new user to the list of Database Administrators:
Database schema mappings let databases that are registered in the directory accept connections from users without requiring any dedicated database schemas for them. For example, when local user Scott connects to a database, a database schema called Scott must exist--for that logon to be successful. This can be difficult to maintain if there are thousands of users and perhaps hundreds of databases in a very large enterprise.
Users that are defined in an LDAP-compliant directory do not require dedicated schemas on every Oracle8i or later database to which they might connect.
A database can use a schema mapping to share one database schema between multiple directory users. The schema mapping is a pair of values: the base in the directory at which users exist, and the name of the database schema they will use.
You can use the Database Schema Mappings tabbed window to manage database schema mappings--when a database is selected under an Oracle Context in the main application tree. This window contains a list of database schema names and Directory Base pairs (Figure 19-13):
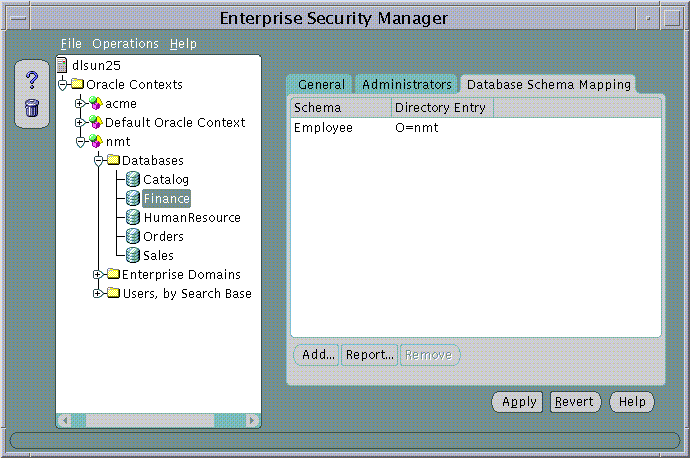
Text description of the illustration esm0020.gif
To remove a mapping from the list of database schema mappings in an enterprise domain:
To add a new mapping to the list of database schema mappings in the enterprise domain:
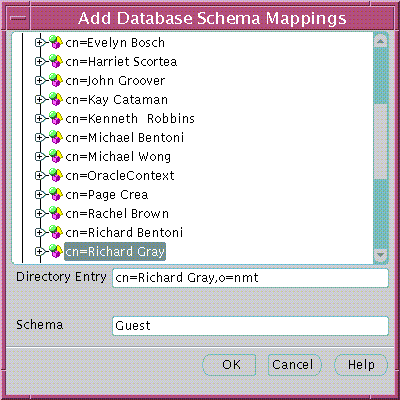
Text description of the illustration esm0021.gif
Use this window to locate and select a base in the directory and pair it with a database schema name, to make a database schema mapping. There are two components to the window: there is a directory search tree from which to select a base, and a field in which to enter a schema name.
An Oracle Context contains at least one enterprise domain called OracleDefaultDomain. The OracleDefaultDomain is part of the Oracle Context when it is first created in the directory. When a new database is registered into an Oracle Context it automatically becomes a member of the OracleDefaultDomain in that Oracle Context. You can create and remove your own enterprise domains but you cannot remove the OracleDefaultDomain from an Oracle Context.
To create a new enterprise domain in an Oracle Context, use either of the following methods:
The Create Enterprise Domain window appears (Figure 19-15):
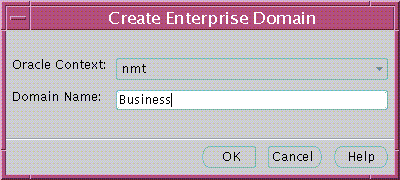
Text description of the illustration esm0023.gif
To create the new enterprise domain:
To remove an enterprise domain:
Use the application tree of the main Oracle Enterprise Security Manager window to select a target enterprise domain. You can then use the Databases tab to manage database membership of an enterprise domain in an Oracle Context (Figure 19-16):
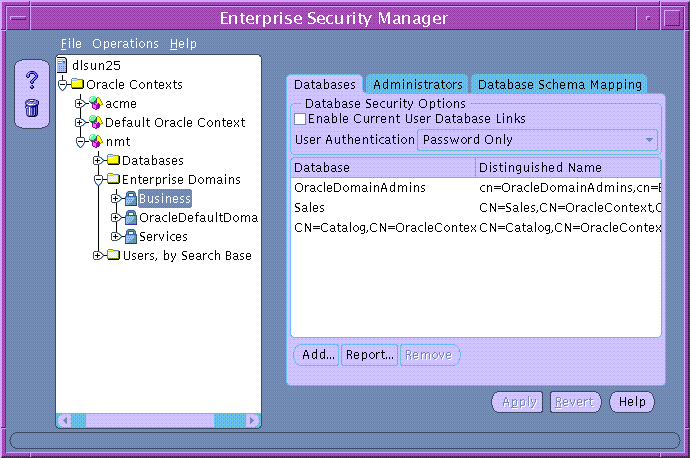
Text description of the illustration esm0025.gif
To remove a database from an enterprise domain:
To add a database to an enterprise domain:
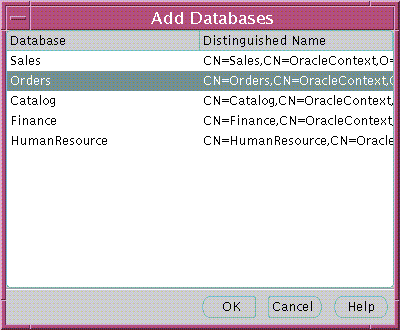
Use the Databases tabbed window (Figure 19-16) to manage database security options applicable to all databases that are members of the enterprise domain.
Database security options are summarized by Table 19-8:
An Enterprise Domain Administrator is a directory user with privileges to modify the content of that domain. You can use the Administrators tabbed window (Figure 19-11) to manage Enterprise Domain Administrators when an enterprise domain is selected under an Oracle Context in the main application tree.
To remove a user from the list of Enterprise Domain Administrators:
To add a new user to the list of Enterprise Domain Administrators:
As previously discussed, database schema mappings can be managed for each database in an Oracle Context. Schema mappings can also be defined for each enterprise domain in an Oracle Context, using the database schema mappings tabbed window with an enterprise domain selected in the main application tree. These mappings apply to all databases that are members of the enterprise domain. Therefore, each database in the enterprise domain must have a schema of the same name used in the mapping for that mapping to be effective on that database.
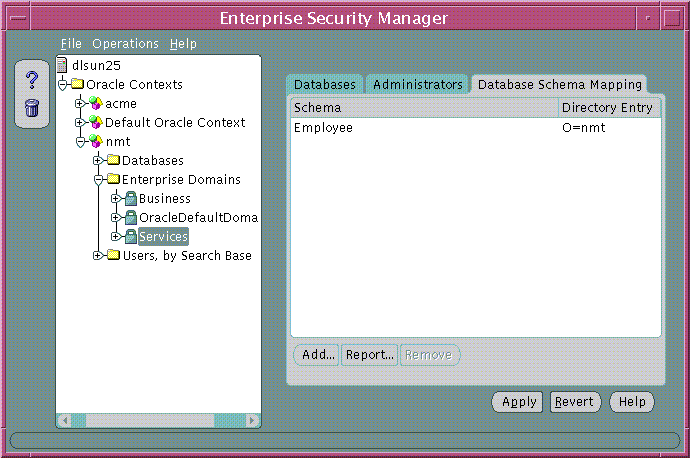
Text description of the illustration esm0027.gif
To remove a mapping from the list of database schema mappings in the enterprise domain (Figure 19-18):
To add a new mapping to the list of database schema mappings in the enterprise domain (Figure 19-18):
An enterprise domain within an Oracle Context can contain multiple enterprise roles. An enterprise role is a set of Oracle role-based authorizations across one or more databases in an enterprise domain.
To create a new enterprise role:
You can create an enterprise role in an enterprise domain either from the Operations menu on the Oracle Enterprise Security Manager main window (Figure 19-18), or by right-clicking an enterprise domain in the main application tree. In either case, the Create Enterprise Role window appears (Figure 19-19):
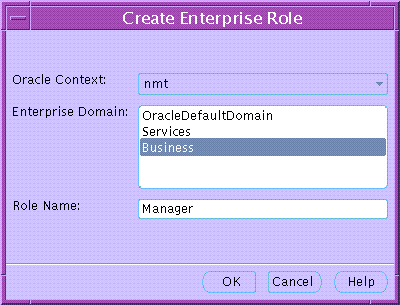
Text description of the illustration esm0030.gif
To remove an enterprise role:
Use the Database Global Roles tabbed window (Figure 19-20) of the Oracle Enterprise Security Manager main window to manage database global role membership in an enterprise role. This window lists the names of each global role that belongs to the enterprise role, along with the name of the database on which that global role exists.
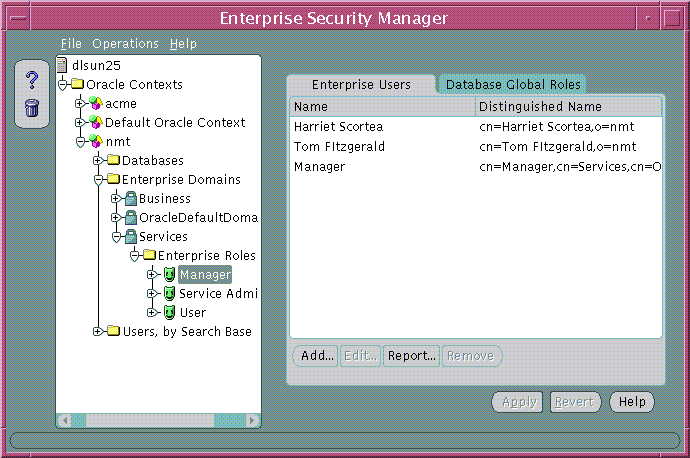
Text description of the illustration esm0031.gif
When populating an enterprise role with different database roles it is only possible to reference roles on databases that are configured to be global roles on those databases. A global role on a database is identical to a normal role, except that the Database Administrator has defined it to be authorized only through the directory. A Database Administrator cannot locally grant and revoke global roles to users of the database.
To remove a database global role from an enterprise role:
To add a global role to an enterprise role:
Text description of the illustration esm0034.gif
An enterprise role grantee is a directory user granted an enterprise role, including all database global roles contained within that enterprise role. You can use the Enterprise Users tabbed window (Figure 19-22) to manage enterprise role grantees, when an enterprise role is selected under an enterprise domain in the main application tree.
To remove a user from the list of enterprise role grantees (Figure 19-22):
To add a new user to the list of enterprise role grantees:
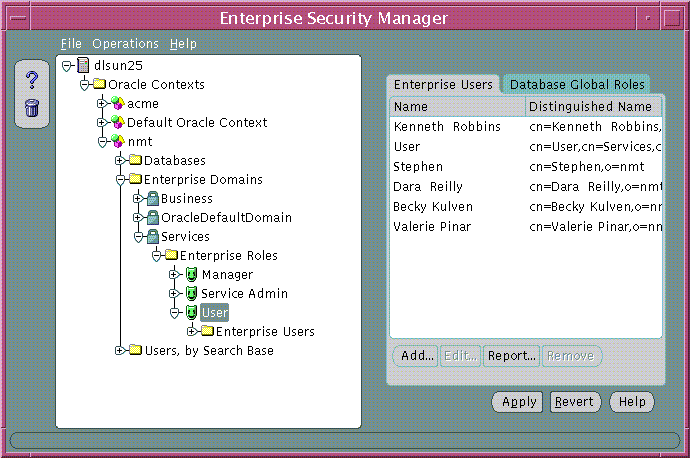
You can assign enterprise roles to this newly created enterprise user by selecting the user and choosing the Enterprise Role tab.
|
 Copyright © 1996, 2002 Oracle Corporation. All Rights Reserved. |
|