![]() Secure Global Desktop 4.40 Administration Guide
> Security
> Security and SGD
Secure Global Desktop 4.40 Administration Guide
> Security
> Security and SGD
| Read This Topic to... |
|---|
|
SGD is only one of many components on your network. The information on this page is related to SGD and can only help raise security levels as part of an ongoing security strategy. The following areas must be considered when using SGD:
SGD connects client devices to application servers, acting as a go-between. SGD servers can also join together as an array.
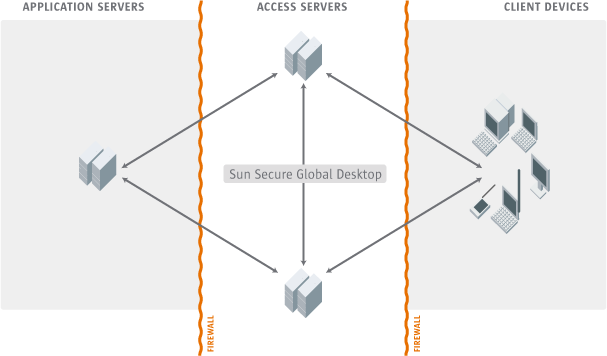
This means the following are the main network connections involved with using SGD:
In a default SGD installation, most connections are unencrypted (in the clear). The following sections describe how you can improve security on network connections.
SGD can also be configured to work with firewalls and proxy servers.
To secure connections between client devices and SGD servers, use a secure (HTTPS) web server on all SGD hosts and enable SGD security services. See Securing Connections Between Client Devices and SGD Servers for more details.
The connections between SGD servers and application servers are used to start applications on the application server, and to send and receive data from the application, such as key presses and display updates.
The level of security between SGD and your application servers depends on the types of application server and the protocols they use.
When using protocols such as telnet or rexec, all communications and passwords are transmitted unencrypted (in the clear).
For secure connections to UNIX or Linux system application servers, use SSH (Secure Shell). SSH encrypts all communications between SGD hosts and encrypts passwords before they are transmitted. See Installing and using SSH with SGD for more information.
By default, SGD secures X displays using X authorization. This prevents users from accessing X displays they are not authorized to access.
The level of security depends on the protocol configured for the Windows application, as follows:
For secure connections to Microsoft Windows application servers, use the Microsoft RDP protocol.
The level of security depends on the type of web server you are using to host the web application:
For secure connections to your web application servers, use HTTPS.
Connections between SGD servers are used to share static and dynamic data across the array. This includes the following:
See Securing Connections Between SGD Servers for details on how to secure these connections.
When logging in to SGD and the SGD Client is in Webtop mode, passwords are only encrypted if there is an HTTPS connection. If the SGD Client is in Integrated mode, the initial connection between the SGD Client and SGD is always secure. After the user is authenticated, the connection might be downgraded to a standard (insecure) connection depending on configuration.
SGD uses external mechanisms for authenticating users:
SGD encrypts all passwords stored in the password cache. By default, the encryption key used for the password cache never changes. You can force the key to change whenever SGD servers start, as follows:
Alternatively, use the following command:
$ tarantella config edit --security-newkeyonrestart 1
Secure Global Desktop Administrators can control users' ability to print and copy data from applications displayed through SGD. You can configure this as follows:
Copyright © 1997-2007 Sun Microsystems, Inc. All rights reserved.